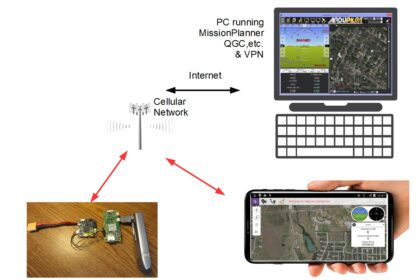
Control Your Plane/Drone over 4G/LTE Telemetry with Ardupilot and Raspberry Pi
Our first featured project dives into the fascinating world of drone telemetry…
Blackmamba: The AI-Powered Polymorphic Malware .
Blackmama is an advanced AI-generated polymorphic malware designed to evade detection by…
Detailed Analysis of Nood RAT Malware
Nood RAT (Remote Access Trojan) is a piece of malware designed to…
In-Depth Analysis of the Polish TicTacToe Dropper
The TicTacToe Dropper, also known as "Kolko_i_krzyzyk" (Polish for "TicTacToe"), is a…
Flipper Zero: A Multifunctional Tool for Ethical Hackers
Flipper Zero is a portable, open-source, multi-tool designed primarily for hardware hacking,…
The Power Of BladeRF
BladeRF is a versatile Software Defined Radio (SDR) platform, primarily used in…
RTL-SDR V4 USB, A Powerful RF Tool for Penetration Testing
The RTL-SDR V4 USB dongle is a versatile and cost-effective software-defined radio…
Malware Persistence Techniques and How To Detect and Remove Persistent Threats.
Persistence is a critical aspect of malware behavior that ensures the malicious…
Mastering Visual Studio Code With These Pro Techniques for Boosting Your Productivity
Visual Studio Code is a powerful tool, much like a finely crafted…