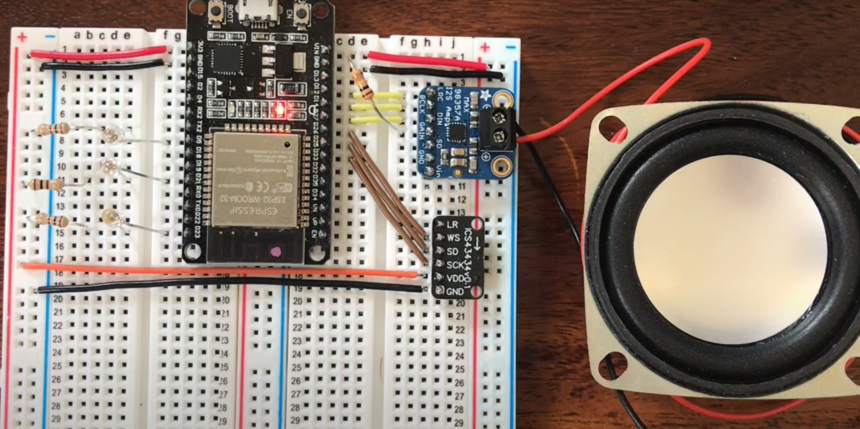
Voice Assistant with ESP32 and TensorFlow Lite.
More Read
Leave a comment Leave a comment
What Do You Consider the Most Challenging Cybersecurity Vulnerability to Mitigate?
- Advanced Persistent Threats (APTs) 50%, 2 votes2 votes 50%2 votes - 50% of all votes
- Phishing and Social Engineering 25%, 1 vote1 vote 25%1 vote - 25% of all votes
- Ransomware 25%, 1 vote1 vote 25%1 vote - 25% of all votes
- Insider Threats 0%, 0 votes0 votes0 votes - 0% of all votes
- Supply Chain Attacks 0%, 0 votes0 votes0 votes - 0% of all votes
- Zero-Day Exploits 0%, 0 votes0 votes0 votes - 0% of all votes
- Cloud Security Misconfigurations 0%, 0 votes0 votes0 votes - 0% of all votes
Total Votes: 4
August 14, 2024 - September 30, 2024
Voting is closed
Thanks for your opinion !











