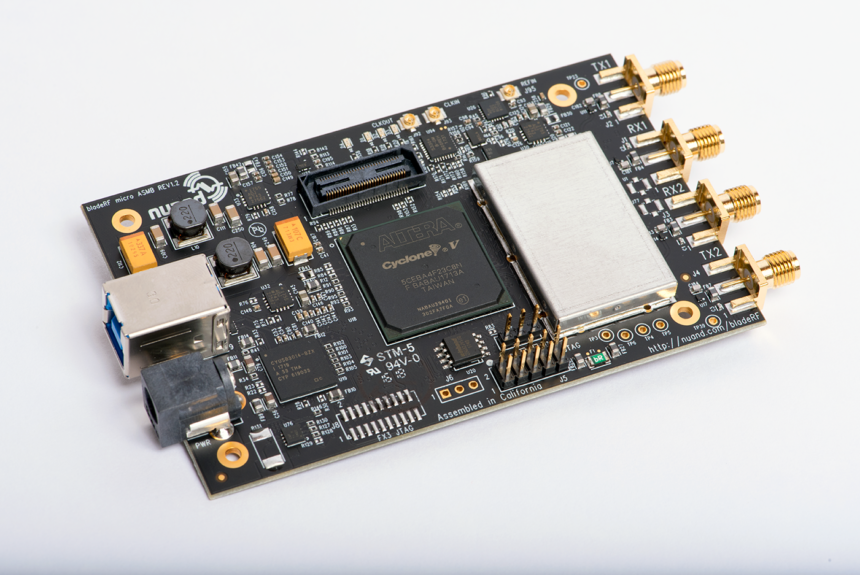
BladeRF is a versatile Software Defined Radio (SDR) platform, primarily used in radio frequency (RF) applications. In the field of penetration testing, BladeRF is utilized for tasks that involve RF signals, such as wireless network penetration testing, signal interception, and manipulation. This includes attacks on wireless protocols like Wi-Fi, Bluetooth, GSM, and other RF-based systems.
Key Uses of BladeRF in Penetration Testing:
- Wireless Network Penetration Testing: BladeRF can be used to sniff, jam, or inject packets into wireless networks. This is particularly useful for testing the security of Wi-Fi networks, as well as for conducting attacks such as deauthentication, man-in-the-middle, and replay attacks.
- GSM and Cellular Network Testing: BladeRF can emulate a GSM base station, allowing a penetration tester to perform attacks on cellular networks, such as intercepting phone calls and SMS messages, or testing the robustness of cellular security implementations.
- Signal Analysis and Reverse Engineering: With BladeRF, you can capture and analyze signals from various wireless devices. This capability is crucial for reverse engineering proprietary wireless protocols, identifying potential vulnerabilities, and developing custom exploits.
- Drone and UAV Testing: BladeRF can be used to test the security of drones and unmanned aerial vehicles (UAVs) by intercepting and manipulating the control signals between the drone and its controller.
- IoT Device Testing: Many IoT devices communicate using RF protocols. BladeRF can be employed to test these devices for security vulnerabilities by capturing, analyzing, and modifying the communication signals.
Example Command to Get Started with BladeRF:
To start using BladeRF with GNU Radio (a toolkit for processing signals), you can install the necessary software and drivers, and then run the following commands in a Linux environment:
# Install GNU Radio and BladeRF libraries sudo apt-get install gnuradio gr-osmosdr libbladerf-dev bladerf # Verify the BladeRF device is detected bladeRF-cli -p
This setup allows you to start building custom RF signal processing and manipulation flows using GNU Radio’s graphical interface.
Examples of how you can use the BladeRF for penetration testing:
Example 1 : Intercepting GSM Communications with BladeRF
BladeRF’s wide frequency range and full-duplex capability make it ideal for intercepting GSM communications. Here’s how you could set up a basic GSM interception scenario using BladeRF:
Tools Required:
- OsmocomBB: An open-source mobile communication software project.
- Kalibrate: Used to identify GSM frequencies.
- GSM-Decoder: For decoding captured GSM traffic.
Step 1 : Install Required Tools.
sudo apt-get install kalibrate-rtl sudo apt-get install gnuradio gnuradio-dev bladerf
Step 2 : Identify Nearby GSM Base Stations.
Use Kalibrate to scan and identify GSM frequencies in your area.
kal -s GSM900 -g 40 -B
Step 3 : Capture GSM Traffic:
Use OsmocomBB with BladeRF to capture GSM traffic.
sudo osmocom_bb -i bladeRF -m GSM900
Step 4 : Decode GSM Traffic.
Use the captured traffic and feed it into GSM-Decoder to decode the conversations or SMS messages.
sudo gsm_decode capture.bin
Note: Intercepting and decoding GSM communications without authorization is illegal. This example should only be used in a controlled environment with permission.
Example 2: Creating a Custom Radio Signal Jammer with BladeRF
BladeRF can be used to create a custom radio signal jammer, useful for testing the robustness of RF systems against interference.
Tools Required:
- GNU Radio: A toolkit for building SDR applications.
- BladeRF: For transmitting the jamming signal.
Step 1: Install GNU Radio and BladeRF Libraries:
sudo apt-get install gnuradio gr-osmosdr libbladerf-dev
Step 2: Create a Jamming Signal Flowgraph:
Use GNU Radio Companion (GRC) to design a jamming signal. A basic flowgraph might consist of a Signal Source generating a continuous wave (CW) or a noise source feeding into a BladeRF sink (output).
Example code snippet for a CW jammer:
import numpy as np
from gnuradio import analog, gr, blocks
class JammingFlowgraph(gr.top_block):
def __init__(self):
gr.top_block.__init__(self)
samp_rate = 2e6
freq = 2.4e9 # Center frequency for jamming
# Generate a continuous wave (CW) signal
source = analog.sig_source_c(samp_rate, analog.GR_COS_WAVE, freq, 1, 0)
# BladeRF sink for transmission
sink = osmosdr.sink(args="bladerf=0")
# Set parameters for BladeRF
sink.set_sample_rate(samp_rate)
sink.set_center_freq(freq)
sink.set_gain(50)
# Connect blocks
self.connect(source, sink)
if __name__ == "__main__":
tb = JammingFlowgraph()
tb.start()
tb.wait()Step 3: Transmit the Signal:
Run your GNU Radio flowgraph to start transmitting the jamming signal.
python jamming_flowgraph.py
Note: Jamming signals can interfere with legal communication services and are illegal in most countries without proper authorization. Ensure this is done in a controlled environment with legal clearance.
As A Summary :
The BladeRF is a high-performance, professional-grade SDR with extensive capabilities, including a wide frequency range, full-duplex operation, and powerful signal processing features, making it suitable for advanced penetration testing and RF development tasks.