Have you ever wondered if your smartphone could be spying on you? In this article, we’re going to explore a particularly dangerous Android spyware known as Spy Note. We’ll dive into its features, how it operates, and most importantly, how you can protect yourself from this silent invader. Whether you’re a tech enthusiast or just someone concerned about privacy, this is crucial information you need to know.
The Android Ecosystem: A Double-Edged Sword
Android is the most popular mobile operating system in the world, with over 3 billion active devices as of June 2021. However, its widespread adoption also makes it a prime target for various types of malware, including spyware, ransomware, adware, and banking trojans. Among these, Spy Note stands out as one of the most notorious threats.
What is Spy Note?
Spy Note is a type of malware known as a Remote Access Trojan (RAT). First discovered in 2016 by Palo Alto Networks, it quickly gained notoriety in underground forums where it was sold for prices ranging from $25 to $200. Marketed as a remote administration tool, Spy Note allows attackers to gain complete control over a victim’s Android device remotely.
The Evolution of Spy Note
Spy Note wasn’t just any ordinary malware; it came equipped with a builder tool that allowed attackers to create customized APK files. These files could be disguised with different icons and names, making them look like legitimate apps. Attackers could then distribute these APK files through various channels, such as SMS phishing campaigns, malicious websites, third-party app stores, or even social media platforms.
How Spy Note Operates
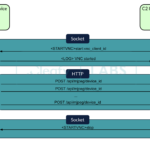
Once installed, Spy Note requests invasive permissions to access various features of the device, such as contacts, location, microphone, camera, storage, phone calls, SMS messages, and accessibility services. If the user unknowingly grants these permissions, the malware hides itself from the home screen and the recent apps menu, making it incredibly difficult to detect or uninstall.
One of the most alarming aspects of Spy Note is that it registers itself as a device administrator. This prevents the user from easily removing the malware. The software then communicates with a command-and-control (C&C) server, which sends commands to the infected device, allowing the attacker to execute a wide range of malicious activities.
The Dangers of Spy Note
Spy Note is particularly dangerous because it does not require root access to operate. This means it can be installed on any Android device, regardless of whether it has been rooted. Some of the malicious activities Spy Note can perform include:
- Recording Audio and Video: Spy Note can record the victim’s audio and video without their knowledge, potentially spying on personal conversations and activities.
- Taking Screenshots: The malware can capture screenshots of the victim’s device, stealing personal information or tracking online activities.
- Tracking GPS Location: Spy Note can monitor the victim’s movements by tracking their GPS location, enabling real-time surveillance.
- Stealing Contacts, Messages, and Call Logs: The malware can harvest the victim’s contacts, SMS messages, and call logs, which can be used for spamming or blackmailing.
- Installing and Uninstalling Apps: Spy Note can install malicious apps or remove security software without the victim’s consent, further compromising the device.
- Executing Arbitrary Commands: The attackers can execute any command on the victim’s device, potentially causing significant damage or stealing more data.
Spy Note’s Disguises: Targeting YouTube Users
Researchers have found that Spy Note often disguises itself as YouTube-related apps, such as “YouTube Music Downloader” or “YouTube Premium Cracker.” Once installed, it can steal account credentials for various services like Facebook, Google, WhatsApp, Instagram, and Twitter. It can even extract Google Authenticator codes used for two-factor authentication, putting your most sensitive accounts at risk.
The Persistence of Spy Note
Removing Spy Note from an infected device is no easy task. The malware employs several techniques to resist removal, including:
- Abusing Accessibility Services: Prevents the user from accessing the settings menu or uninstalling apps.
- Broadcast Receivers: Automatically restarts itself if terminated by the system or user.
- Diehard Services: Runs in the background even when the device is in sleep mode.
- Root Privileges: If it gains root access, Spy Note can hide itself from antivirus apps or security scanners, making detection nearly impossible.
How to Protect Yourself from Spy Note
Given the severity of the threat posed by Spy Note, it is crucial to take steps to protect yourself and your device. Here are some best practices:
- Install Apps from Trusted Sources: Only download apps from the Google Play Store or official websites. Avoid third-party app stores or downloading APK files from unknown sources.
- Be Cautious with Permissions: Before installing an app, check what permissions it requests. Deny any permission that seems unnecessary or suspicious.
- Avoid Clicking on Suspicious Links: Do not click on links or open attachments in unsolicited SMS messages or emails. These could lead to malicious websites or download harmful files.
- Use Security Software: Regularly scan your device with a reputable antivirus app or security scanner to detect any signs of infection.
- Keep Your Device Updated: Ensure that your device is running the latest security patches and firmware updates to protect against known vulnerabilities.
- Regular Backups: Regularly back up your data to a secure cloud service or external storage device. This ensures you can recover your data in case of a malware infection or if a factory reset becomes necessary.
- Disable Installation from Unknown Sources: On Android devices, you can disable the installation of apps from unknown sources. For instance, on Samsung devices, go to Settings > Apps > Special App Access > Install Unknown Apps and disable permissions for apps you don’t trust.
Final Thoughts
Spy Note is a dangerous Android trojan that gives attackers complete control over a victim’s device. Its ability to operate without root access and its persistence in resisting removal make it particularly threatening. To safeguard your device from Spy Note and other similar malware, it is essential to follow the security tips outlined above.
If you found this information helpful, please consider sharing it with others who might benefit from it. Your awareness and caution can make a significant difference in protecting your privacy and security. Stay safe and vigilant!