Pretty Good Privacy (PGP) is a cryptographic software package designed to provide secure communication. Developed by Phil Zimmermann in 1991, it has become a cornerstone of email security and data protection. PGP offers a suite of cryptographic tools to encrypt, decrypt, sign, and verify data, ensuring confidentiality, integrity, and authenticity.
1.How PGP Works
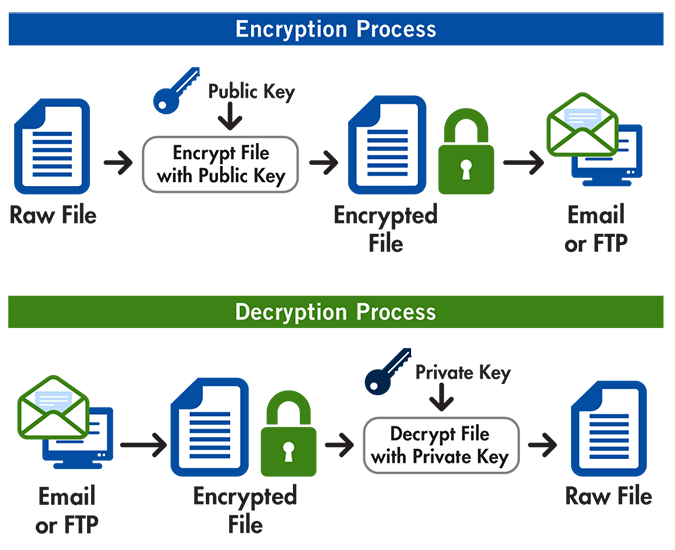
PGP employs a hybrid cryptosystem, combining the strengths of symmetric and asymmetric encryption.
- Key Generation: A PGP user generates a key pair: a public key and a private key. The public key can be shared freely, while the private key must be kept secret.
- Encryption: To send a secure message, the sender uses the recipient’s public key to encrypt the message with a randomly generated symmetric key. This symmetric key is also encrypted using the recipient’s public key and appended to the message.
- Decryption: The recipient uses their private key to decrypt the symmetric key and then uses it to decrypt the actual message.
- Digital Signatures: PGP also provides digital signatures to verify the authenticity and integrity of messages. The sender uses their private key to create a digital signature, which is appended to the message. The recipient uses the sender’s public key to verify the signature.
2.Use Cases of PGP
PGP has a wide range of applications, including:
- Email Encryption: Protecting sensitive email content from unauthorized access.
- File Encryption: Securing confidential files by encrypting them before storage or transmission.
- Disk Encryption: Encrypting entire disk partitions to safeguard sensitive data.
- Digital Signatures: Verifying the authenticity and integrity of documents and software.
3.Essential PGP Projects
While PGP itself is a standard, several open-source implementations and commercial products offer PGP-based encryption:
- GnuPG (GPG): A free software implementation of the OpenPGP standard, widely used in various operating systems and applications.
- PGP Corporation: Offers commercial PGP software with additional features and support.
- Keybase: A platform that provides PGP key management, secure messaging, and file sharing.
4.The Mathematics Behind PGP

PGP relies on several cryptographic algorithms:
- Symmetric Encryption: Commonly uses AES (Advanced Encryption Standard) for efficient encryption and decryption.
- Asymmetric Encryption: Employs RSA (Rivest-Shamir-Adleman) or Elliptic Curve Cryptography (ECC) for key exchange and digital signatures.
- Hash Functions: SHA-256 or SHA-512 are used to create message digests for digital signatures.
These algorithms provide the mathematical foundation for PGP’s security.
let’s dive deeper into the mathematical magic behind RSA key generation process as PGP predominantly relies on RSA for asymmetric cryptography:
- Prime Number Selection: Two distinct, large prime numbers,
pandq, are randomly chosen. - Modulus Calculation: The product of these primes,
n = p * q, forms the modulus. - Totient Calculation: Euler’s totient function, φ(n) = (p-1)(q-1), is calculated. This represents the number of positive integers less than
nthat are relatively prime ton. - Public Exponent Selection: A public exponent,
e, is chosen such that1 < e < φ(n)andeis co-prime toφ(n). A common choice ise = 65537. - Private Exponent Calculation: The private exponent,
d, is calculated such that(e * d) mod φ(n) = 1. This is typically done using the Extended Euclidean Algorithm.
The public key is the pair (n, e), while the private key is (n, d).
While the mathematics of key generation is relatively straightforward, key distribution is a complex issue. PGP primarily relies on the following methods:
- Direct Key Exchange: This involves physically transferring the public key to the recipient. While secure, it’s impractical for large-scale communication.
- Key Servers: Public key servers act as repositories for public keys. Users can upload their public keys to these servers, and others can retrieve them. However, the security of these servers is crucial.
- Web of Trust: This is a decentralized approach where users vouch for the authenticity of other users’ public keys. It relies on trust relationships between users.
5.Challenges and Considerations
- Key Management:Safeguarding private keys is crucial. Lost or compromised keys can lead to data loss. it is arguably the most critical aspect of PGP. It’s the process of generating, distributing, using, storing, and revoking cryptographic keys. A compromised key can render the entire system vulnerable.
- Complexity: PGP can be complex to set up and use for non-technical users.
- Interoperability: Compatibility issues may arise between different PGP implementations.
- Quantum Computing Threat: Advances in quantum computing could potentially break RSA and ECC, impacting PGP’s security.