OnionShare is an open-source tool that allows you to share files, host websites, and even chat with friends securely and anonymously using the Tor network.
- Secure File Sharing: Share files directly from your computer without revealing your identity.
- Anonymous Website Hosting: Create and host websites accessible only through the Tor network.
- Private Chat: Communicate with others securely and anonymously.
- Peer-to-Peer Sharing: Leverages the Tor network for enhanced privacy and anonymity.
How it Works:
OnionShare uses the Tor network to create a unique address (onion address) for your computer. This address is used to share files, access your website, or connect with others. By routing your traffic through multiple Tor relays, your identity remains hidden.:
- Sharing sensitive files: Safely share confidential documents without fear of exposure.
- Whistleblowing: Anonymously share information with journalists or human rights organizations.
- Protecting privacy: Communicate and share files without revealing your personal information.
How to use OnionShare:
OnionShare is available for Windows, macOS, and Linux. The installation process varies slightly depending on your operating system.
General Steps:
- Download: Visit the official OnionShare website and download the appropriate version for your system.
- Installation: Follow the on-screen instructions to install OnionShare. This usually involves running an installer file and accepting the default settings.
- Launch: Once installed, find the OnionShare application in your applications menu and open it.
Specific Instructions:
For more detailed instructions, refer to the official OnionShare documentation
If you encounter issues or prefer a command-line installation, you can find additional options on the OnionShare GitHub repository:
Using OnionShare:
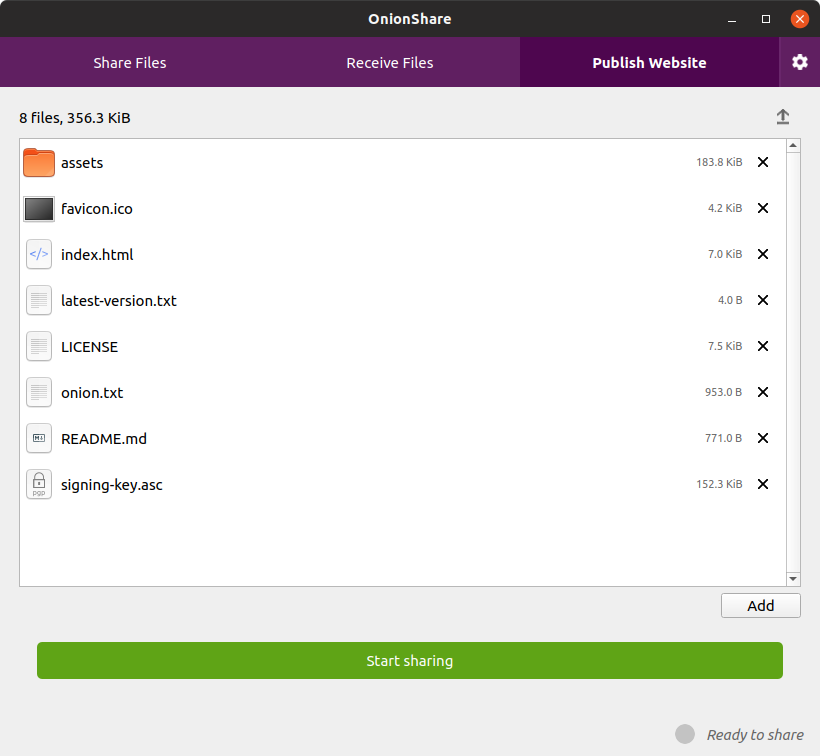
Once OnionShare is installed and running, you’ll see a user interface with several options.
Sharing Files:
- Click on the “Share File” button.
- Select the file you want to share.
- OnionShare will generate an onion address.
- Share this address with the recipient. They will need the Tor Browser to access the file.
Hosting a Website:
- Click on the “Share Website” button.
- Select the folder containing your website’s files.
- OnionShare will generate an onion address for your website.
- Share this address with others to access your website through the Tor Browser.
Note: Ensure you have Tor installed and running on your system for OnionShare to function correctly.
Additional Tips:
- Consider checking that you’re connected to Tor Network before using OnionShare
- For added security, consider using a strong password for your OnionShare instance.
- Be aware that the speed of file sharing and website loading can be affected by your internet connection and the Tor network’s traffic.
- For more advanced usage, explore OnionShare’s settings and command-line options.