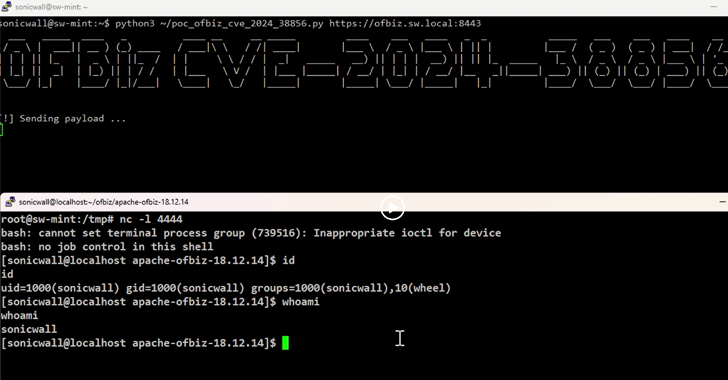
A severe vulnerability has been identified in the Apache OFBiz ERP system that could allow attackers to remotely execute code on vulnerable systems. The zero-day flaw, designated CVE-2024-38856, has been assigned a critical CVSS score of 9.8, indicating a high potential for exploitation.
The vulnerability, discovered by SonicWall, originates from a weakness in the authentication mechanism. This flaw enables unauthorized individuals to access functionalities typically requiring login credentials, ultimately leading to remote code execution. Notably, CVE-2024-38856 bypasses a previously patched path traversal vulnerability (CVE-2024-36104).
The specific issue lies within the override view functionality, which exposes critical endpoints to unauthenticated attackers. By exploiting this weakness through carefully crafted requests, malicious actors can gain unauthorized access and execute arbitrary code.
This is the latest in a series of critical vulnerabilities affecting Apache OFBiz. Previous zero-day flaws, including CVE-2024-32113 and CVE-2023-51467, have also been actively exploited for malicious purposes.
Organizations utilizing Apache OFBiz versions prior to 18.12.15 are strongly advised to prioritize the application of the available patch to mitigate the risk of exploitation.