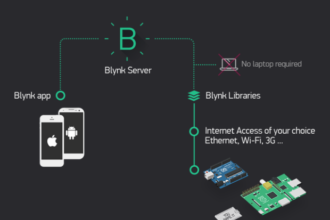
Build Your Own IoT Mobile App With Blynk.
Blynk is an IoT platform that allows you to easily build mobile and web applications to control various hardware projects.…
The Symbiosis Between Defensive and Offensive Techniques in Cybersecurity
Cybersecurity is an ongoing battle between defenders and attackers, each group employing sophisticated methods to outmaneuver the other. Both sides,…
Understanding Zero Trust Network Access (ZTNA) Security and Implementation
Zero Trust Network Access (ZTNA) is a category of technologies that ensure secure remote access to applications and services by…
Malware Persistence Techniques and How To Detect and Remove Persistent Threats.
Persistence is a critical aspect of malware behavior that ensures the malicious software remains active and continues to execute after…
Nmap : A Beginner’s Guide to the most powerful network reconnaissance
Nmap (short for Network Mapper) is a powerful and versatile network reconnaissance tool widely used by hackers, security professionals, and…
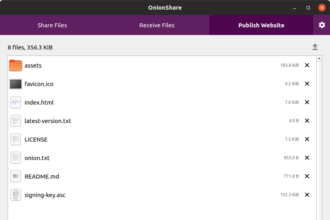
OnionShare: Secure and Anonymous Sharing
OnionShare is an open-source tool that allows you to share files, host websites, and even chat with friends securely and…
An 18 Years old girl published an AI assistant that helps generate cybersecurity payloads .
The landscape of cybersecurity is constantly evolving, demanding innovative solutions to combat emerging threats. Payload Wizard, an AI assistant devolopped…
The Dark Side of APK Obfuscation: Malicious Use Cases
What is APK Obfuscation? APK obfuscation is a process that transforms the code within an Android Package (APK) file into…
BlackArch: A Comprehensive Guide
Understanding BlackArch: A Penetration Tester's Toolbox Before we dive into specific tools and techniques, let's solidify our understanding of BlackArch.…
A Comprehensive Guide to Installing BlackArch
Choosing a Virtualization Platform Several virtualization platforms are available, each with its strengths and weaknesses. Here are some popular options:…