Why Pixhawk Stands Out: A Technical Comparison of Flight Controllers.
Pixhawk is a widely-used open-source hardware platform for autopilot and drone control, developed by the PX4 community. It is employed…
How hackers are making millions selling video game cheats ?
Hackers have found a highly profitable niche by developing and selling cheats for video games, generating millions in revenue annually.…
$16.5 Million Lottery Scam That Shook America’s Lotteries.
In one of the most elaborate lottery scams in history, a man with inside access managed to rig lottery numbers,…
Cryptocurrency Companies in the Crosshairs: FBI Issues Warning on North Korean Hacking Threats
The FBI has issued a new warning highlighting the aggressive tactics employed by North Korean hacking groups targeting cryptocurrency companies.…
The Critical Microsoft IPv6 Buffer Overflow Vulnerability
In recent months, a critical vulnerability known as CVE-2024-38063 has emerged, putting millions of Windows systems at risk. This vulnerability,…
Binance Seizes Palestinian Accounts.
In a significant turn of events, the cryptocurrency exchange Binance has recently been involved in seizing accounts associated with Palestinian…
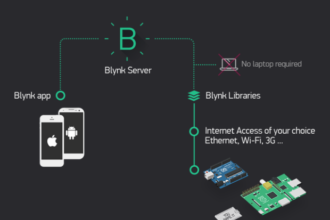
Build Your Own IoT Mobile App With Blynk.
Blynk is an IoT platform that allows you to easily build mobile and web applications to control various hardware projects.…
The Symbiosis Between Defensive and Offensive Techniques in Cybersecurity
Cybersecurity is an ongoing battle between defenders and attackers, each group employing sophisticated methods to outmaneuver the other. Both sides,…
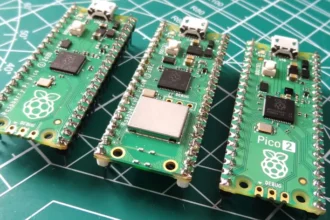
Overview and Review of The New Raspberry Pico 2
The Raspberry Pi Pico 2 is an evolution of the original Raspberry Pi Pico, which made waves in the microcontroller…
Understanding Zero Trust Network Access (ZTNA) Security and Implementation
Zero Trust Network Access (ZTNA) is a category of technologies that ensure secure remote access to applications and services by…