Tracking the Trump Shooter’s Phone
Researchers have meticulously mapped the movements of Thomas Matthew Crooks's phone leading up to the day of the failed…
DePIN: Decentralizing the Physical World
DePIN, short for Decentralized Physical Infrastructure Networks, represents a groundbreaking concept that marries the digital realm of blockchain with the…
A nice Do It Yourself project: Rubber Ducky using Arduino Uno or D1 board
A Rubber Ducky is essentially a USB device disguised as a harmless object (like a rubber duck) that, when plugged…
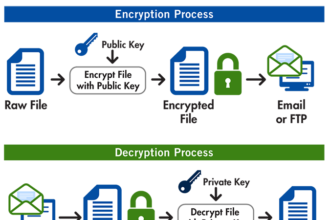
PGP: Pretty Good Privacy Explained
Pretty Good Privacy (PGP) is a cryptographic software package designed to provide secure communication. Developed by Phil Zimmermann in 1991,…
Cython: Bridging Python and C for Performance
Cython is a programming language and compiler that serves as a bridge between Python and C. It allows you to…
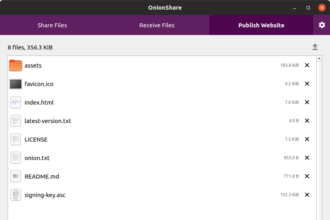
OnionShare: Secure and Anonymous Sharing
OnionShare is an open-source tool that allows you to share files, host websites, and even chat with friends securely and…
Python Libraries Dark Side: RAT Development
Python, a versatile and beginner-friendly language, has unfortunately become a tool of choice for cybercriminals to develop Remote Access Trojans…
An 18 Years old girl published an AI assistant that helps generate cybersecurity payloads .
The landscape of cybersecurity is constantly evolving, demanding innovative solutions to combat emerging threats. Payload Wizard, an AI assistant devolopped…
The Dark Side of APK Obfuscation: Malicious Use Cases
What is APK Obfuscation? APK obfuscation is a process that transforms the code within an Android Package (APK) file into…
A Comprehensive overview about most used Vim features.
Vim, a powerful text editor, offers a vast array of features to streamline text editing. While the "most used" features…