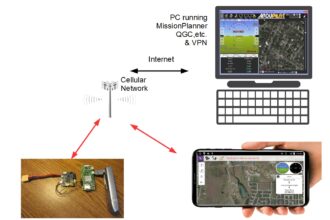
Control Your Plane/Drone over 4G/LTE Telemetry with Ardupilot and Raspberry Pi
Our first featured project dives into the fascinating world of drone telemetry using 4G/LTE technology. This hands-on guide, powered by…
Flipper Zero: A Multifunctional Tool for Ethical Hackers
Flipper Zero is a portable, open-source, multi-tool designed primarily for hardware hacking, cybersecurity research, and penetration testing. Resembling a toy,…
Detailed Analysis of Nood RAT Malware
Nood RAT (Remote Access Trojan) is a piece of malware designed to remotely control infected systems, allowing attackers to perform…
In-Depth Analysis of the Polish TicTacToe Dropper
The TicTacToe Dropper, also known as "Kolko_i_krzyzyk" (Polish for "TicTacToe"), is a sophisticated malware delivery mechanism that has been actively…
Blackmamba: The AI-Powered Polymorphic Malware .
Blackmama is an advanced AI-generated polymorphic malware designed to evade detection by continuously altering its code. Imagine a criminal who…
The Power Of BladeRF
BladeRF is a versatile Software Defined Radio (SDR) platform, primarily used in radio frequency (RF) applications. In the field of…
RTL-SDR V4 USB, A Powerful RF Tool for Penetration Testing
The RTL-SDR V4 USB dongle is a versatile and cost-effective software-defined radio (SDR) device that has become an essential tool…
Airavat RAT Analysis
Airavat is a sophisticated Android Remote Access Trojan (RAT) with a GUI-based web panel that does not require port forwarding.…
Malware Persistence Techniques and How To Detect and Remove Persistent Threats.
Persistence is a critical aspect of malware behavior that ensures the malicious software remains active and continues to execute after…
Mastering Visual Studio Code With These Pro Techniques for Boosting Your Productivity
Visual Studio Code is a powerful tool, much like a finely crafted instrument. Its true potential is unlocked only when…