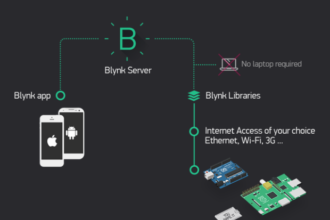
Build Your Own IoT Mobile App With Blynk.
Blynk is an IoT platform that allows you to easily build mobile and web applications to control various hardware projects.…
U.S. Offers Up to $2.5M Reward for Information on Belarusian Cybercriminal.
The U.S. Department of State has announced a reward of up to $2.5 million for information leading to the arrest…
Qilin Ransomware : A New Polymorphic Malware attacking sensitive Industries.
Qilin is an advanced strain of ransomware leverages novel techniques to infiltrate systems, evade detection, and steal sensitive data before…
LM Studio 0.3.0 : New Updates !
LM Studio 0.3.0, released in August 2024, brings several significant updates that enhance its functionality and user experience, especially for…
The Symbiosis Between Defensive and Offensive Techniques in Cybersecurity
Cybersecurity is an ongoing battle between defenders and attackers, each group employing sophisticated methods to outmaneuver the other. Both sides,…
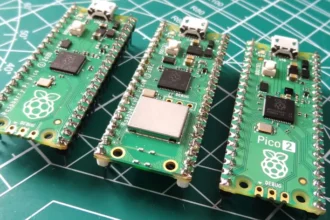
Overview and Review of The New Raspberry Pico 2
The Raspberry Pi Pico 2 is an evolution of the original Raspberry Pi Pico, which made waves in the microcontroller…
Understanding Zero Trust Network Access (ZTNA) Security and Implementation
Zero Trust Network Access (ZTNA) is a category of technologies that ensure secure remote access to applications and services by…