In a concerning development within the cybersecurity landscape, a massive phishing campaign dubbed “Echo Spoofing” has come to light. This operation exploited a vulnerability within Proofpoint, a leading cybersecurity firm that provides email security services to numerous Fortune 100 companies. The attackers were able to send tens of millions of perfectly spoofed emails from well-known brands, including IBM, Disney, and Nike, leveraging a flaw in the default SPF (Sender Policy Framework) records used by Proofpoint’s email protection service.
This article delves into the technical details of the Echo Spoofing campaign, the vulnerabilities exploited, the scale of the attack, and the subsequent measures taken to mitigate the threat.
Understanding SPF and Its Role in Email Security
SPF is a widely adopted email authentication protocol that specifies which mail servers are permitted to send emails on behalf of a domain. It serves as a critical defense mechanism against email spoofing, where attackers forge the sender’s address to make emails appear as though they are from a legitimate source.
In practice, SPF records are stored in the Domain Name System (DNS) and list the IP addresses or hostnames authorized to send emails for a particular domain. When an email is received, the receiving mail server checks the SPF record to verify whether the sender is authorized. If the SPF check fails, the email can be flagged as suspicious or rejected altogether.
The Proofpoint Vulnerability:
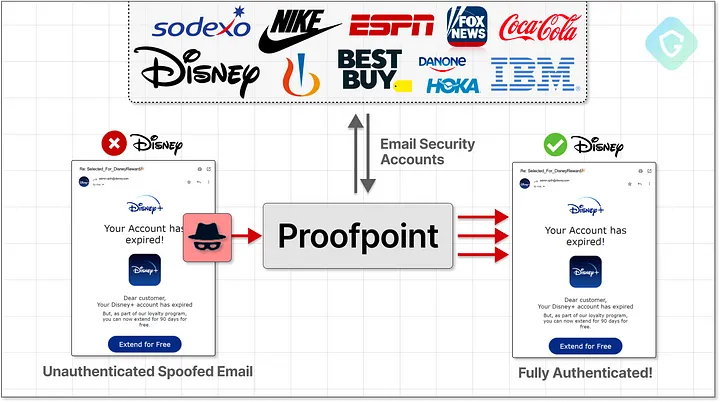
Proofpoint’s email protection service is designed to prevent email spoofing and other email-borne threats. However, a critical flaw was discovered in the default SPF records for customers using Microsoft Outlook as their email platform. The default configuration allowed any emails sent from Office 365 to be accepted and relayed by Proofpoint, regardless of the actual sender.
This misconfiguration effectively bypassed the SPF checks that are supposed to prevent spoofing, allowing cybercriminals to send emails that appeared to come from legitimate domains. These emails were indistinguishable from genuine messages, even including signatures that identified them as being from trusted brands like Disney.
The Echo Spoofing Campaign
The Echo Spoofing campaign, discovered by cybersecurity firm Guardio, capitalized on this vulnerability to launch a massive phishing operation. Since January 2024, the campaign has been sending an estimated average of 3,000,000 phishing emails per day, with the volume peaking at 14,000,000 emails on one particular day.
The phishing emails were crafted to appear as if they were sent from reputable companies such as IBM, Disney, and Nike. The attackers used these spoofed emails to target both consumers and employees within these companies, aiming to steal sensitive information such as login credentials, financial data, and other personally identifiable information (PII).
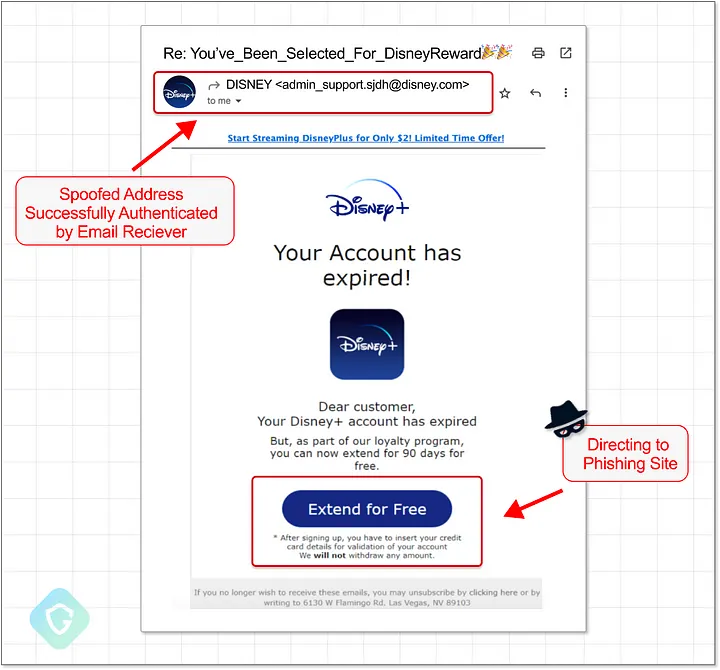
The effectiveness of the campaign was amplified by the fact that the spoofed emails passed through Proofpoint’s email protection service, which is trusted by many organizations to filter out malicious content. As a result, recipients were more likely to trust the emails, increasing the likelihood of successful phishing attempts.
Discovery and Mitigation

Guardio, the cybersecurity firm that uncovered the Echo Spoofing campaign, reported the vulnerability to Proofpoint, which quickly took action to address the issue. Proofpoint has since updated its systems to mitigate the risk of further exploitation.
One of the key steps taken was the creation of a new admin panel that allows organizations to specify which Microsoft tenant domains are authorized to send emails on their behalf. This update helps ensure that only legitimate emails are relayed through Proofpoint’s email protection service, reducing the risk of spoofing.
In addition to the technical fix, Proofpoint has also engaged in outreach efforts to inform its customers about the vulnerability and the steps needed to secure their email systems. This includes guidance on properly configuring SPF records and other email authentication protocols such as DKIM (DomainKeys Identified Mail) and DMARC (Domain-based Message Authentication, Reporting, and Conformance).
Guard.io made a great article giving more details about this topics : you can check out this link for more infos.
Thanks for reading, stay informed !












