Editor's Pick
20 Must-Have Browser Extensions for Ethical Hackers and OSINT Investigators
When it comes to finding vulnerabilities associated with a website or utilizing…
Ransomware Attack on Paris Museums
Insights from Darkweb and Threat Actors.
Follow US
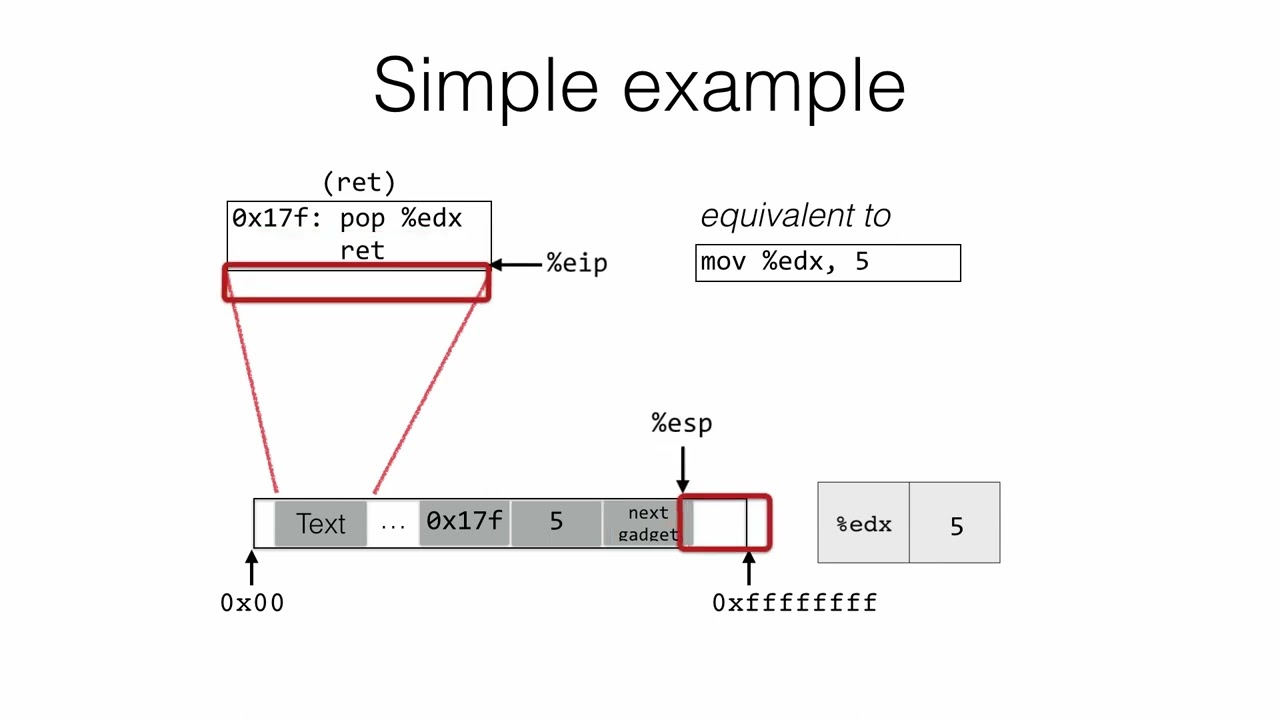
Videos of the month
Discover More
The Critical Microsoft IPv6 Buffer Overflow Vulnerability
In recent months, a critical vulnerability known as CVE-2024-38063 has emerged, putting millions of Windows systems at risk. This vulnerability, identified in the IPv6 implementation within the Windows TCP/IP stack,…
GitHub Vulnerability: Deleted and Private Repository Data are Not Safe
If you've ever assumed that your private or deleted GitHub repositories are secure and inaccessible, it's time to reconsider. A…
U.S. and Russia Swap High-Profile Cybercriminals in Largest Prisoner Exchange Since Cold War
In a significant geopolitical event reminiscent of Cold War-era diplomacy, the United States and Russia executed the largest prisoner exchange…
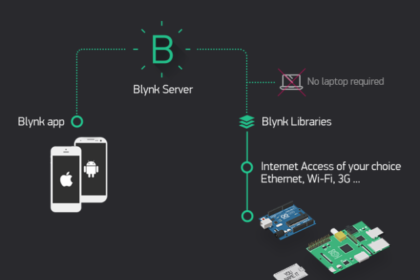
Build Your Own IoT Mobile App With Blynk.
Blynk is an IoT platform that allows you to easily build mobile and web applications to control various hardware projects.…
New Research Reveals 1 Million Domains at Risk of Being Hijacked
Recent research has unveiled a concerning cybersecurity threat, revealing that over one million domain names are at risk of being hijacked by cybercriminals. The threat, referred to as the "sitting…
Detailed Analysis of Nood RAT Malware
Nood RAT (Remote Access Trojan) is a piece of malware designed to remotely control infected systems, allowing attackers to perform…
Airavat RAT Analysis
Airavat is a sophisticated Android Remote Access Trojan (RAT) with a GUI-based web panel that does not require port forwarding.…
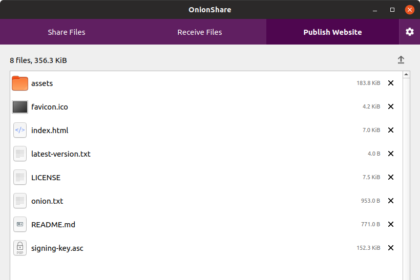
OnionShare: Secure and Anonymous Sharing
OnionShare is an open-source tool that allows you to share files, host websites, and even chat with friends securely and…
- Advanced Persistent Threats (APTs) 50%, 2 votes2 votes 50%2 votes - 50% of all votes
- Phishing and Social Engineering 25%, 1 vote1 vote 25%1 vote - 25% of all votes
- Ransomware 25%, 1 vote1 vote 25%1 vote - 25% of all votes
- Insider Threats 0%, 0 votes0 votes0 votes - 0% of all votes
- Supply Chain Attacks 0%, 0 votes0 votes0 votes - 0% of all votes
- Zero-Day Exploits 0%, 0 votes0 votes0 votes - 0% of all votes
- Cloud Security Misconfigurations 0%, 0 votes0 votes0 votes - 0% of all votes
Thanks for your opinion !